The cyber threat landscape is ever evolving. Hence, an IT System which was delivered correctly yesterday, may not be safe today. Threats are events that exploit vulnerabilities to do harm to an organisation’s assets. To prevent these potential harm, an organisation will identify new vulnerabilities and either rectify the vulnerabilities or mitigate the risks to an acceptable level.
In this article, we will be focusing on Vulnerability Assessment and Penetration Testing.
Vulnerability Assessment (VA) is to define, identify, classify and prioritise the discovery of vulnerabilities within the defined scope of the IT System(s). There are various forms of Vulnerability Assessment where tools such as scanners are used to discover vulnerabilities. The types of VA is determined by the target systems, e.g. Operating System VA is to discover any vulnerabilities through the OS layer, Network VA is to discover any vulnerabilities(including application types) through the network layer. The two most common Web-based VA are Static Application Security Testing (SAST) and Dynamic Application Security Testing (DAST). Interactive Application Security Testing (IAST) is the combination of SAST and DAST.
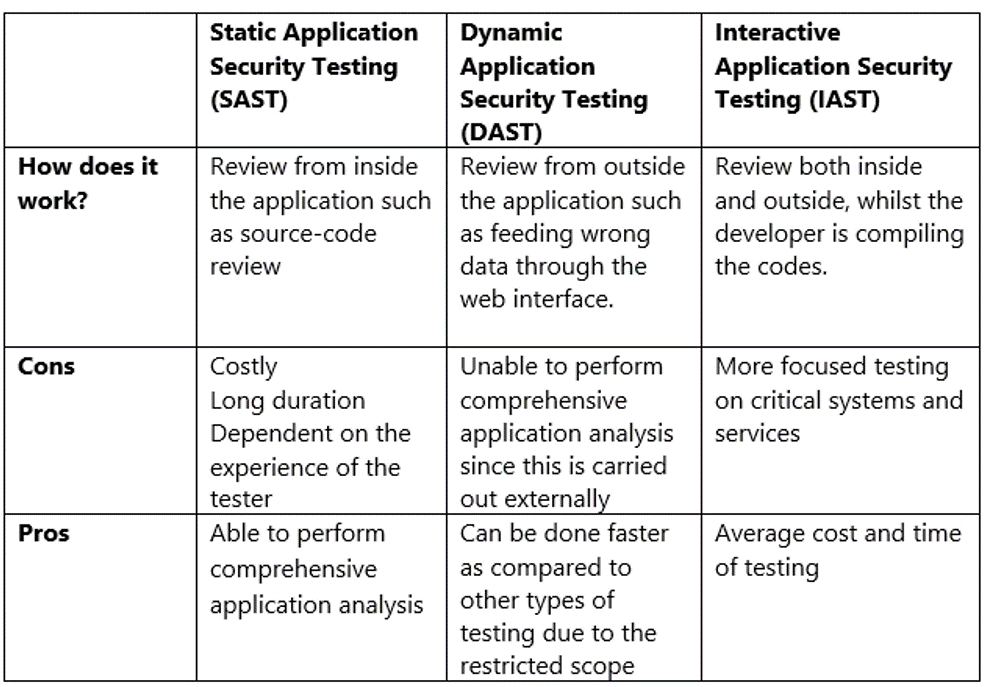
The type of VA should be determined based on the defined scope of the VAPT. For example, there’s no point doing a SAST for Commercial-Out-Of-The-Box software, but a DAST on COTS can discover new vulnerabilities. There’s no point doing Operating System VA on Network appliances, since the Network appliance OS is pre-hardened and (usually) evaluated on the Common Criteria (CC) guidelines. Minimally a Network VA should be done on an IT System, which has been wholesale migrated to a new network. The Network VA will be able to discover any misconfigured network parameters.
Penetration Testing is when the discovered vulnerability cannot be rectified. The tester will try to exploit the vulnerability to determine the extent of the damage that can be done, if at all. There are 3 types of PT, described in the box below.
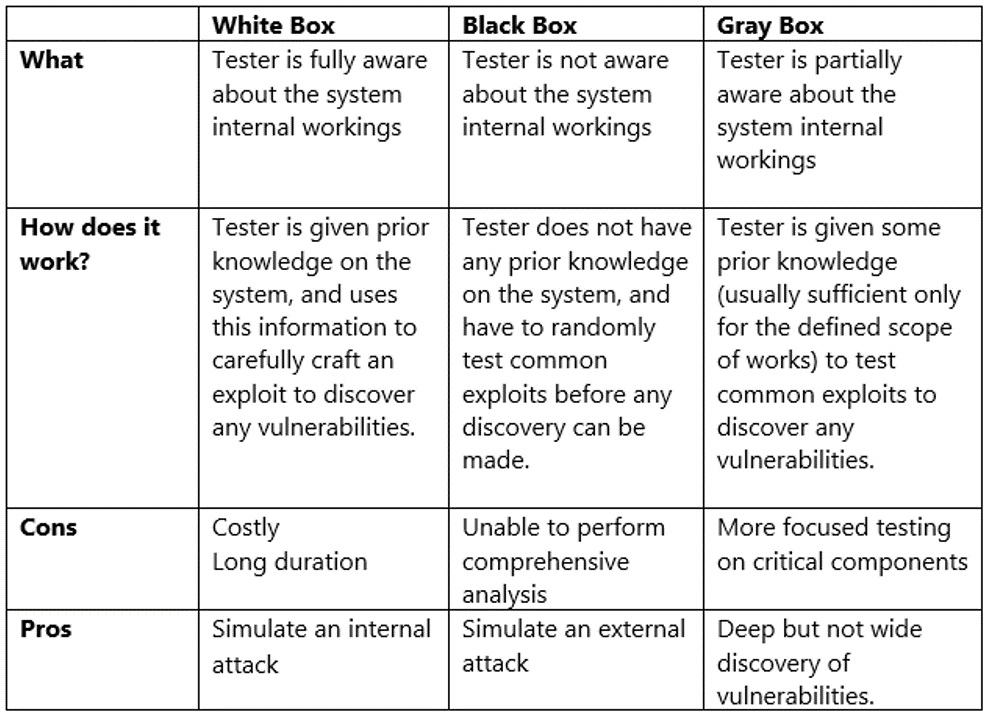
The difference between Vulnerability Assessment and Penetration Testing is that the former discovers security flaws present in the organization’s system whereas the latter is used to show how damaging it can be should the vulnerabilities be exploited.
“Vulnerability Assessment is mostly automatic by tools, but Penetration Testing is a hybrid of tools and manual techniques.”
This VA/PT methodology is widely accepted by most security auditing firms. Almost all typical companies do not do their own VAPT but engage external auditors to execute the VA/PT. Depending upon the business objectives, different scope of the VA/PT will be planned. When a vulnerability is discovered, and it cannot be rectified, a PT is done to determine the extent of the potential damage should the vulnerability be exploited. This is the basis of the risk assessment to determine if additional security controls should be implemented. Not all vulnerabilities can be rectified. Some have no patch available as yet ( e.g. zero – day ), some may have no support today, ( e.g. legacy products ), and some may not be applicable, as determined by the PT.






